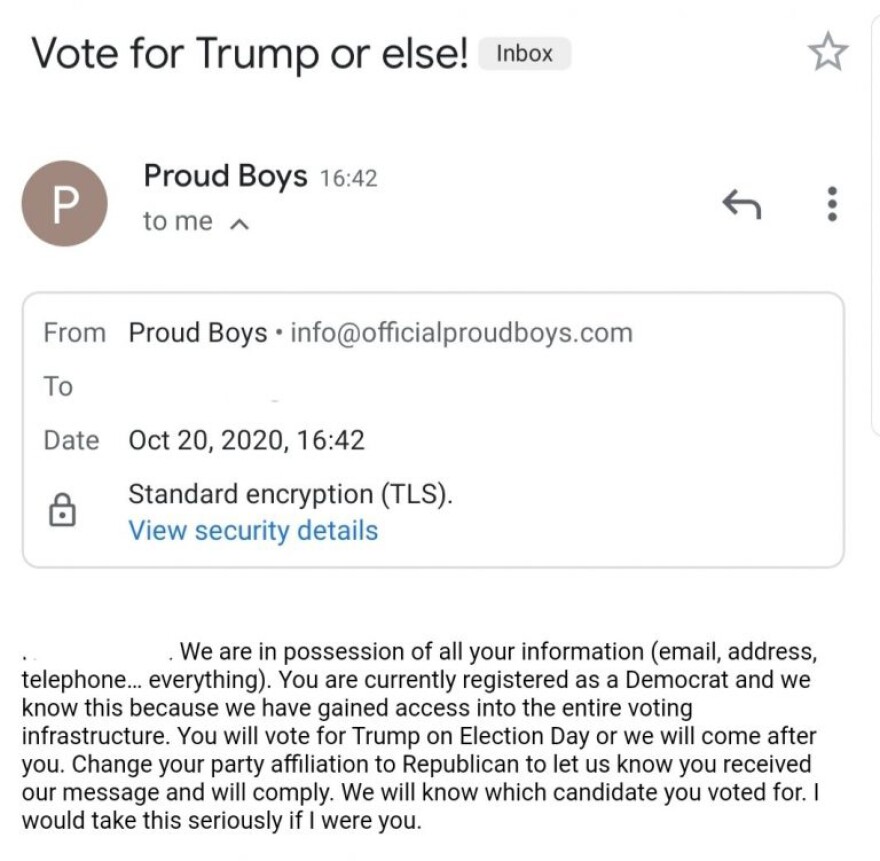
Democratic voters in Florida reported receiving threatening emails Tuesday purportedly from the violent, far-right group Proud Boys directing them to vote for President Donald Trump or “we will come after you.”
The head of the Proud Boys in Florida said in an interview that his group was not responsible for the email threats.
The FBI and the Alachua County Sheriff’s Office were investigating, according to sheriff’s spokesman Art Forgey. The county elections office here said “dozens” of Democratic voters complained they had received the emails. At least some registered Democrats did not.
Registered Democrats who received the emails live in Alachua County – one of only nine counties in Florida where Trump lost in 2016 and home to the University of Florida campus. Later in the day Democrats elsewhere in Florida from Brevard, Charlotte and Clay counties also reported receiving them.
The chairman of Proud Boys, Enrique Tarrio of Miami, said his group did not send the emails. He made the remarks in an interview with Fresh Take Florida, a news service operated by the University of Florida College of Journalism and Communications. Tarrio said he was cooperating with the FBI’s investigation.
“We don't do mass emails,” Tarrio said. “This is definitely, definitely not us.”
Tarrio also said the Proud Boys had no history of being involved in voter intimidation.
“It’s just never been a thing,” Tarrio said.
Proud Boy groups and their affiliates have been encouraging their supporters in recent weeks to join the Trump campaign’s Election Day operations, urging them to register as poll watchers.
Florida is crucially important in the upcoming presidential election, and political polls show a remarkably close race here in recent weeks.
“When I clicked it and read more, I was like, this has to be illegal,” said Jessica McCroan, 24, of Gainesville, who received one of the emails before noon. She called police and county election officials.
McCroan said she already voted by mail and was upset about what she described as voter intimidation tactics.
“I just can't believe that people are doing this, when we should be pushing people to vote, not making them scared to go vote,” she said.
The email said it came from the Proud Boys, an extremist group active in Florida that has openly supported Trump and has engaged in violent clashes in cities around the United States. Among the group’s supporters is Roger Stone, an occasional adviser to Trump who was imprisoned on charges of witness tampering and lying to investigators until Trump pardoned him this summer.
Stone, who lives in Florida, did not immediately respond to an email or a phone call to his lawyer’s office.
When Trump was asked about the Proud Boys during the presidential debate last month, and whether he would condemn white supremacists, he answered: “Proud Boys, stand back and stand by.” He said the following day that he had intended to tell the group to “stand down.”
In the email, the perpetrators ominously claimed to have “gained access into the entire voting infrastructure,” but that boast appeared exaggerated: Thousands of registered Democrats in Florida include their email addresses and phone numbers in the state’s voter registration records, which are publicly available to anyone who requests them.
The email also warned recipients by name that the group knew their address, email address, telephone number and “everything” – however, those details are generally included in the same voter registration records.
“We will know which candidate you voted for,” the email said, though ballot selections are secret under Florida law. The email directed Democrats to change their party affiliation to Republican “to let us know you received our message and will comply.”
Attempting to threaten or intimidate voters in federal elections is a federal crime punishable by fines and up to one year in prison.
A computer scientist at Johns Hopkins University in Maryland, Max Zinkus, examined the routing information inside one of the threatening emails and said it traced back to a computer server in Saudi Arabia. He said the email appeared to be created on a management interface common on older web servers with known software vulnerabilities that render them accessible to hackers.
Zinkus said it’s possible the digital breadcrumbs on the emails were falsified to throw off investigators. “It’s also possible that someone compromised a device and used it to connect to this Saudi server, or compromised the Saudi server itself, or both,” said Zinkus, a doctoral student who studies security, privacy and cryptography.
The emails were made to appear they were sent from a computer server associated with the officialproudboys.com internet address, but control over that account – which was originally created in March 2017 – was changed Monday night, according to internet records. That website was offline by Tuesday afternoon.
The identities of those behind the officialproudboys.com address was shielded in internet records, but they used an email address with a German suffix and were customers of the company 1&1 IONOS Inc. of Chesterfield, Pennsylvania. A company spokesman could not immediately be reached for comment.
___
This story was produced by Fresh Take Florida, a news service of the University of Florida College of Journalism and Communications. The reporter can be reached at adeluca@freshtakeflorida.com